Johann Penner, Chairman of the ECG Hanover

Electronic Access Control Systems
Modern access control with extensive reader portfolio and wireless smartlocks – always the right solution for every door.
Powerful access control
The right solution for every door
doorLoxx® is our comprehensive access control system and provides an easy and cost-effective way to switch from a conventional locking system to a fully-fledged electronic access control system. The extensive product portfolio always offers the optimal solution for every type of door.
Important high-traffic doors such as the main entrance are controlled with an online reader and controller. Office doors and meeting rooms can be managed at the click of a mouse using offline cylinders and electronic fittings. All other conventional keys are automatically managed in our electronic key cabinets.





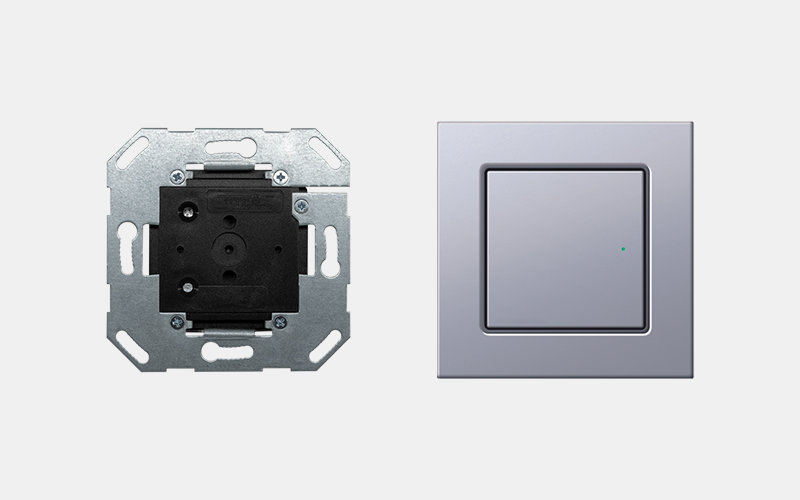
Online reader
Elegant and high quality
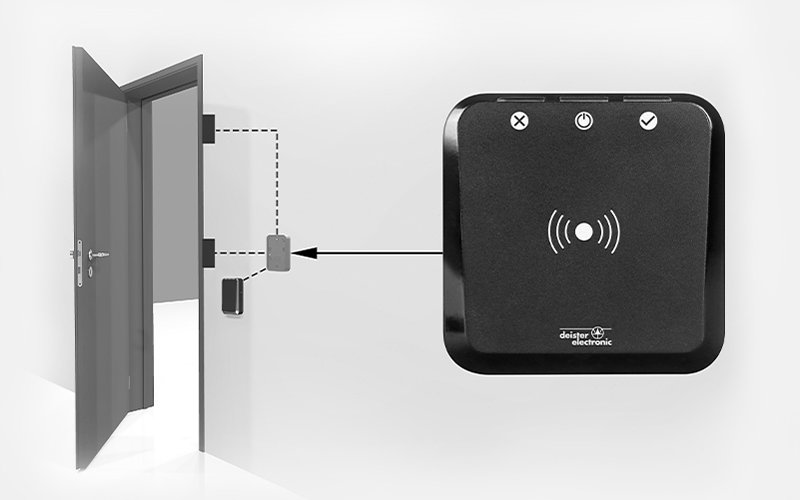
Offline reader
Battery powered readers
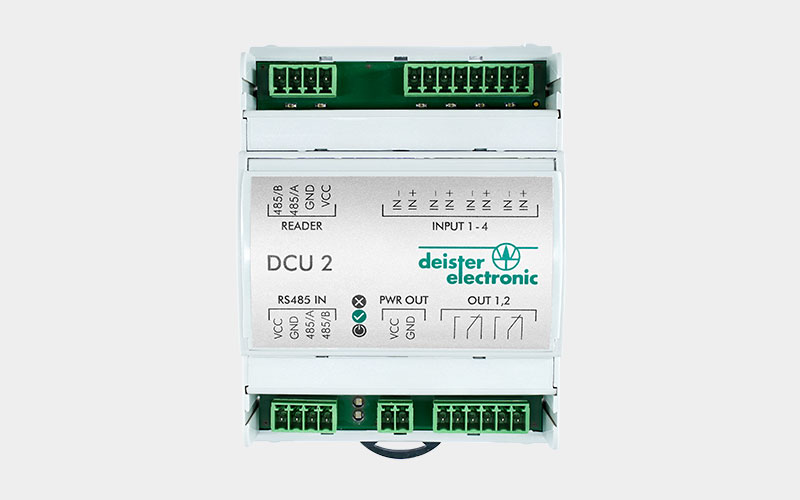
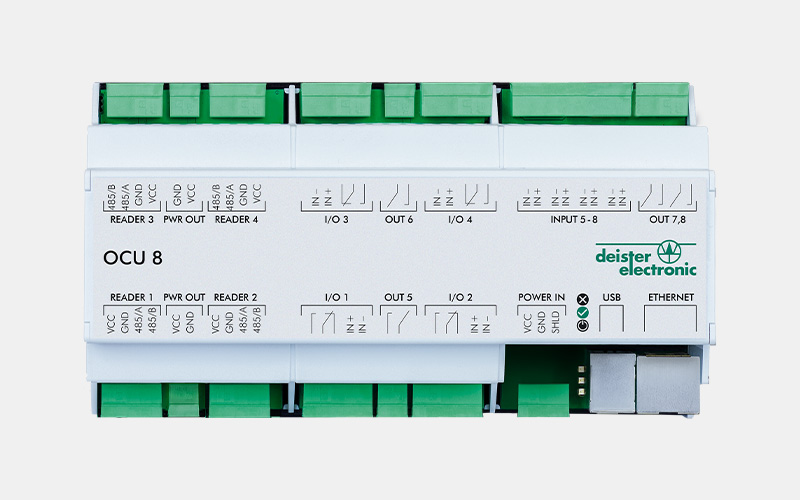
Controller
Intelligent door control
Ident media
The secure ID card
Benefits of our solution

Highly secure, yet simply managed
Simple and safe - It's possible
Security and simplicity are difficult to combine. Our doorLoxx® access control solution was designed with security in mind right from the start. Security-by-design enables easy handling of credentials and readers without compromising on security.

Cost efficiency
The right solution for every door
Not every door is the same, therefore not every reader is suitable for every door. There are different types of doors in a building (e.g. from the main entrance to the office door) with varying security requirements. With our extensive product portfolio, we provide the appropriate, cost-effective solution for every door.

Bluetooth®
Futureproof
Using smartphones as ID cards offers completely new possibilities and flexibility and can be used in our access control system as an alternative or as the only ID for a user. For this purpose, both the online readers and the battery-powered readers can be equipped with a BLE interface.
Our app and cloud infrastructure provide highly secure communication between devices to meet current IT security standards. The data remains highly encrypted from its origin in our software until it is processed in the reader.
Videos
References

Hafven Hannover
The Hafven - Hanover's innovative, combined coworking space and maker area - relies on an intelligent and holistic security solution from deister electronic. It keeps unauthorised persons out without restricting the creative community's freedom of movement.

ECG Hanover
An intelligent, user-friendly access control and key management system from deister electronic ensures enhanced security and transparency at the community center of the Evangelical Christian Church (ECG) in Hanover.

Wiener Wohnen
A complete electronic access control solution with scheduling for all laundry rooms in the residential complexes managed by Wiener Wohnen Haus- & Außenbetreuung GmbH has been developed by the Regensburg-based systems house GemiTeam GmbH together with ACONDA systems GmbH based in Vienna. Each RFID reader was pre-tested by deister electronic and delivered in consistently high quality.